How to setup verified commits on GitHub

Luis Falcon
Frontend Developer

In the world of software development, maintaining the integrity and authenticity of code is paramount. One effective way to enhance this security is through verified commits using GPG (GNU Privacy Guard). In this comprehensive guide, we'll explore the steps involved in setting up verified commits, providing you with a solid foundation for ensuring the trustworthiness of your codebase.
Verified commits are particularly valuable for open-source projects and collaborations where multiple contributors are involved. By leveraging GPG, developers can cryptographically sign their commits, establishing a clear chain of trust and safeguarding against unauthorized changes.
In this post, we'll cover everything you need to know, from installing and configuring GPG to signing your commits and understanding the verification process. Whether you're new to cryptographic signatures or seeking to enhance your project's security, this guide will walk you through the essential steps, demystifying the process along the way.
Creating GPG Keys
First, you need to generate a GPG Key pair. Your GPG Key must use RSA with a key size of 4096 bits.
gpg --full-generate-key
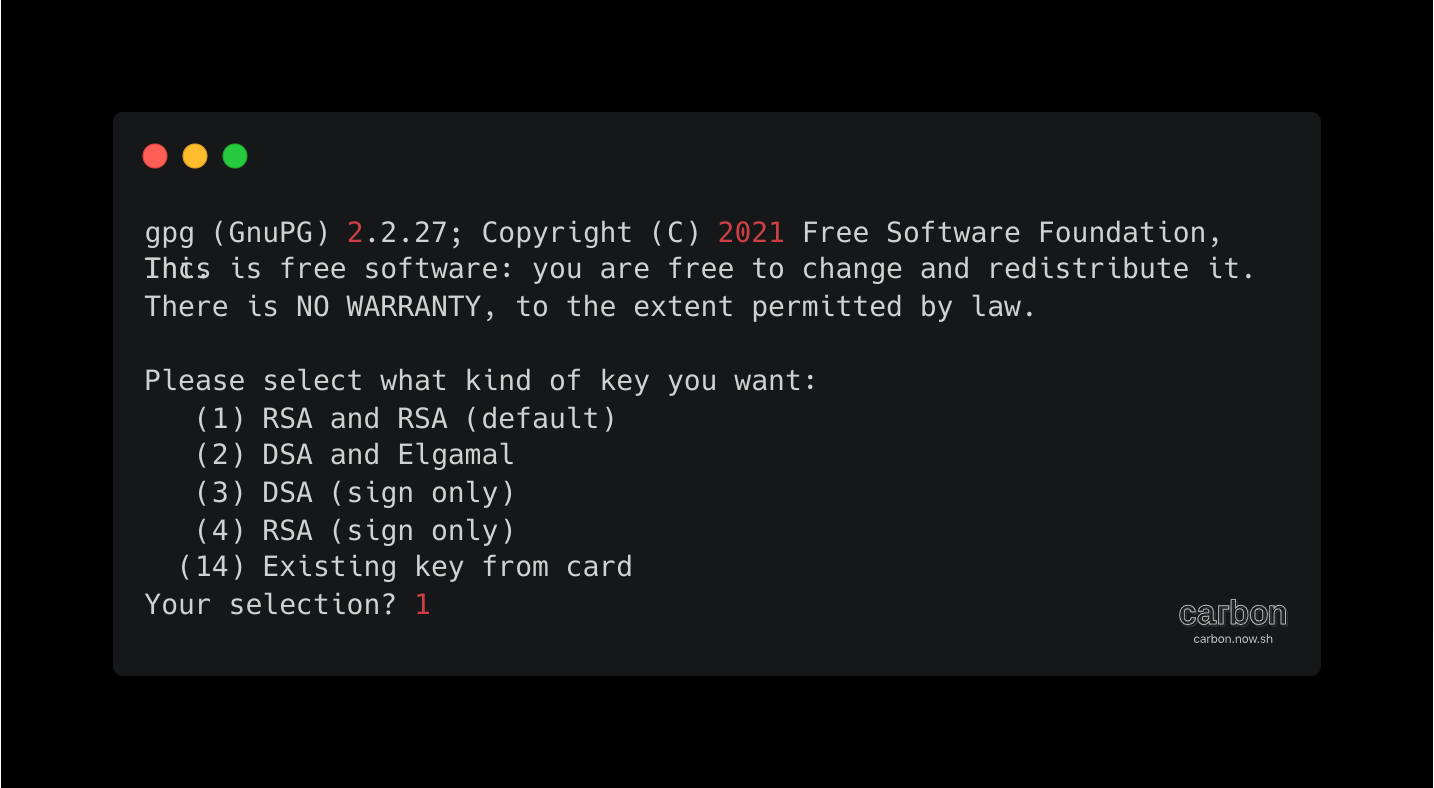
At the prompt, specify the kind of key you want, or press Enter to accept the default RSA.
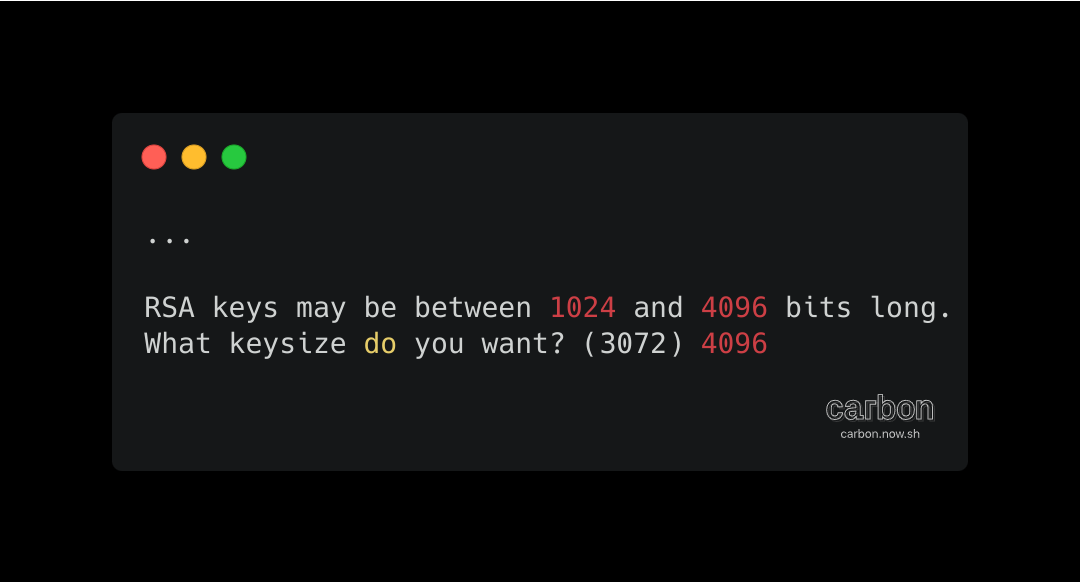
Enter the desired key size. I recommend the maximum key size of 4096.
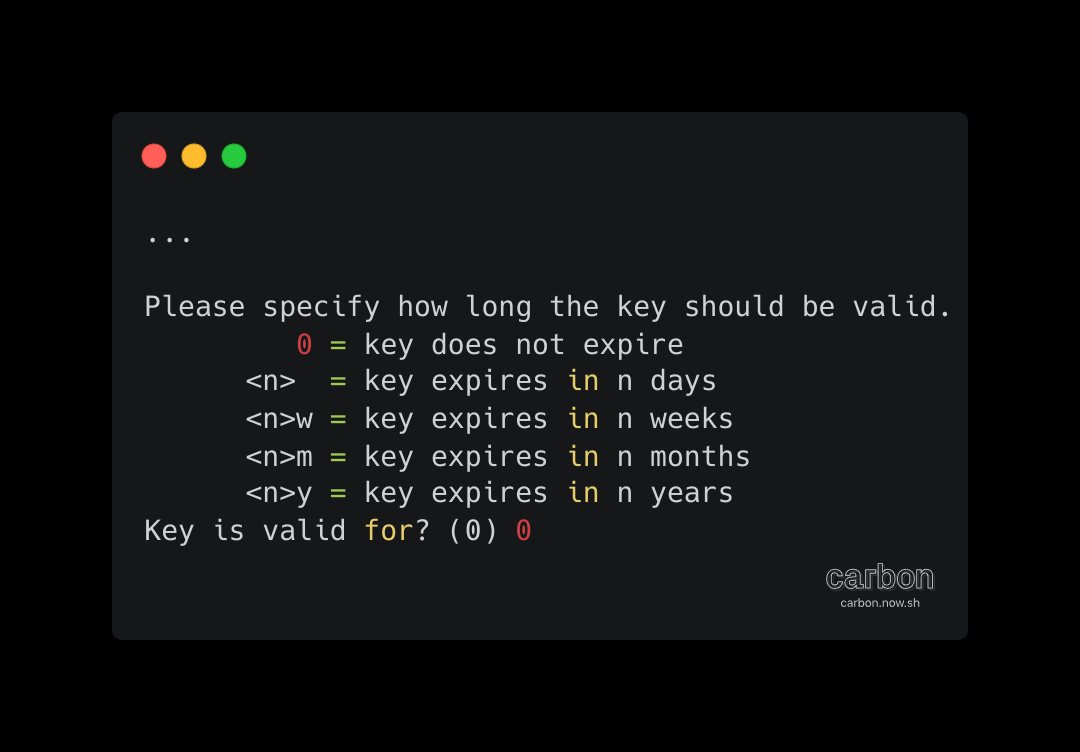
Enter the length of time the key should be valid. Press Enter to specify the default selection, indicating that the key doesn't expire.
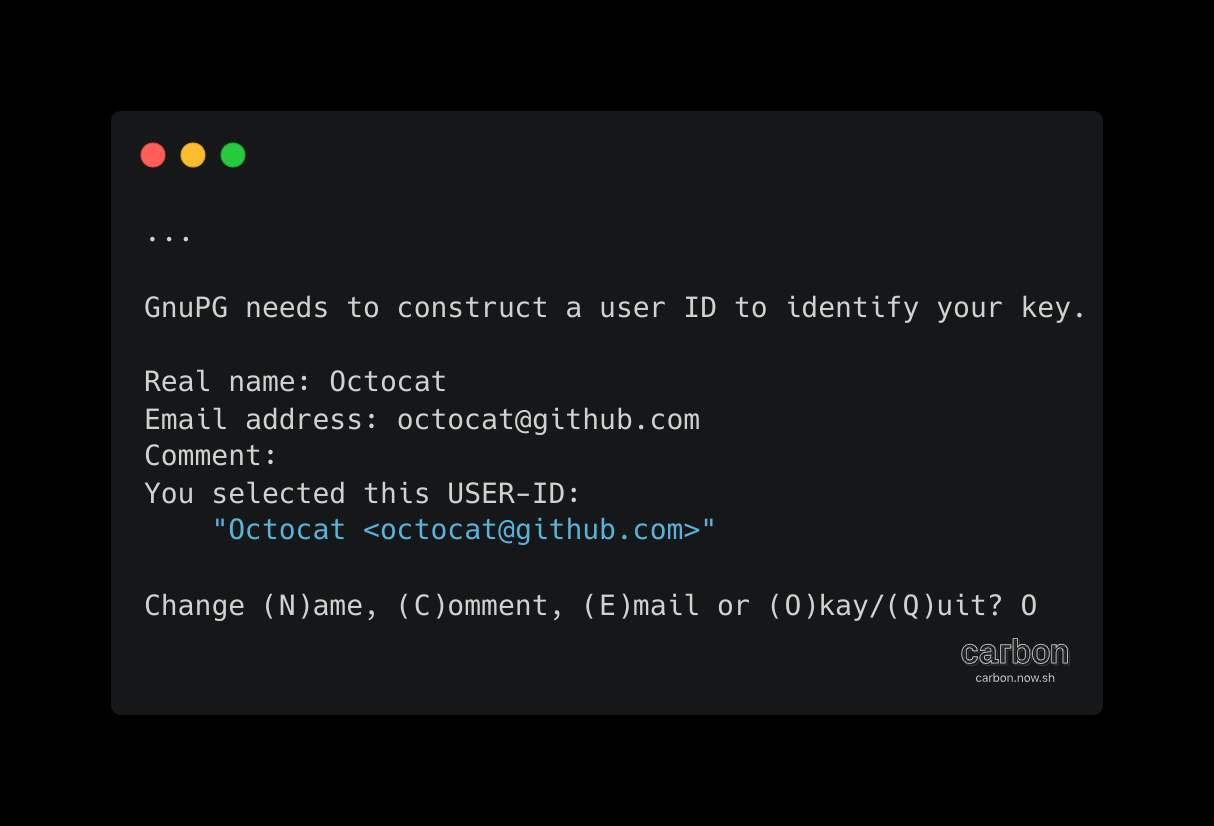
Verify that your selections are correct and enter your user ID information.
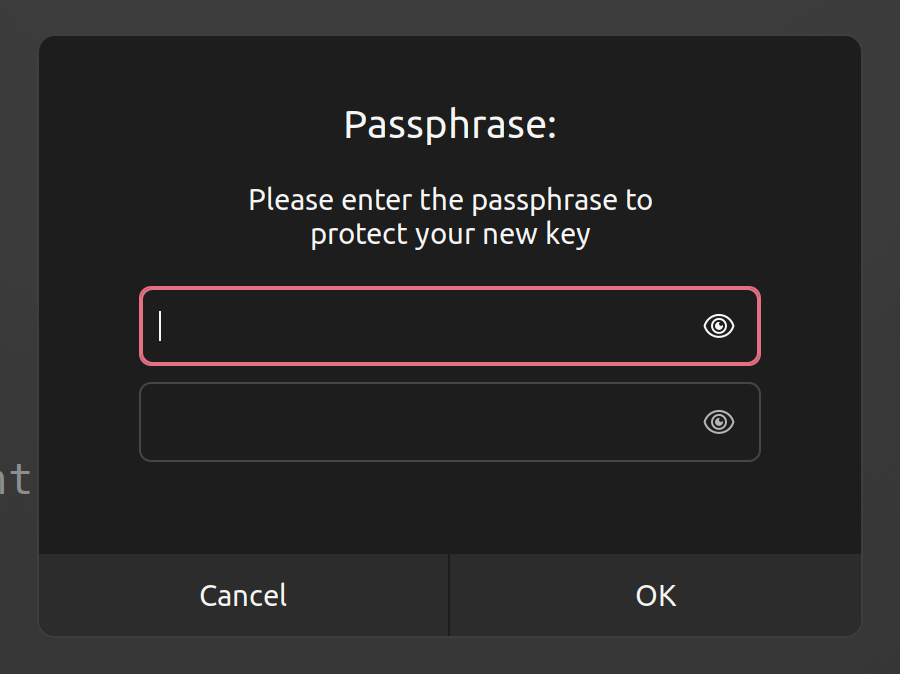
Type a secure passphrase. Remember, you need to use this phrase on each commit created or when trying to use a SSH operation.
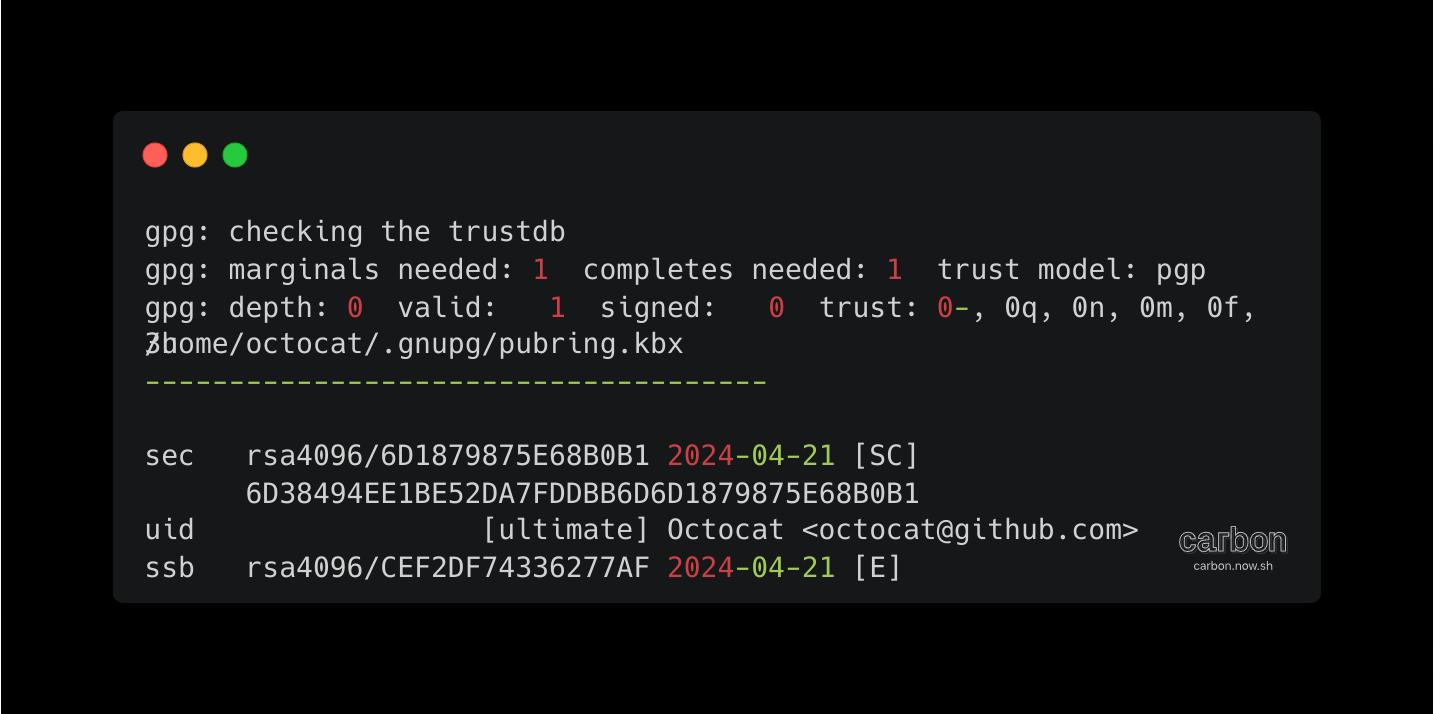
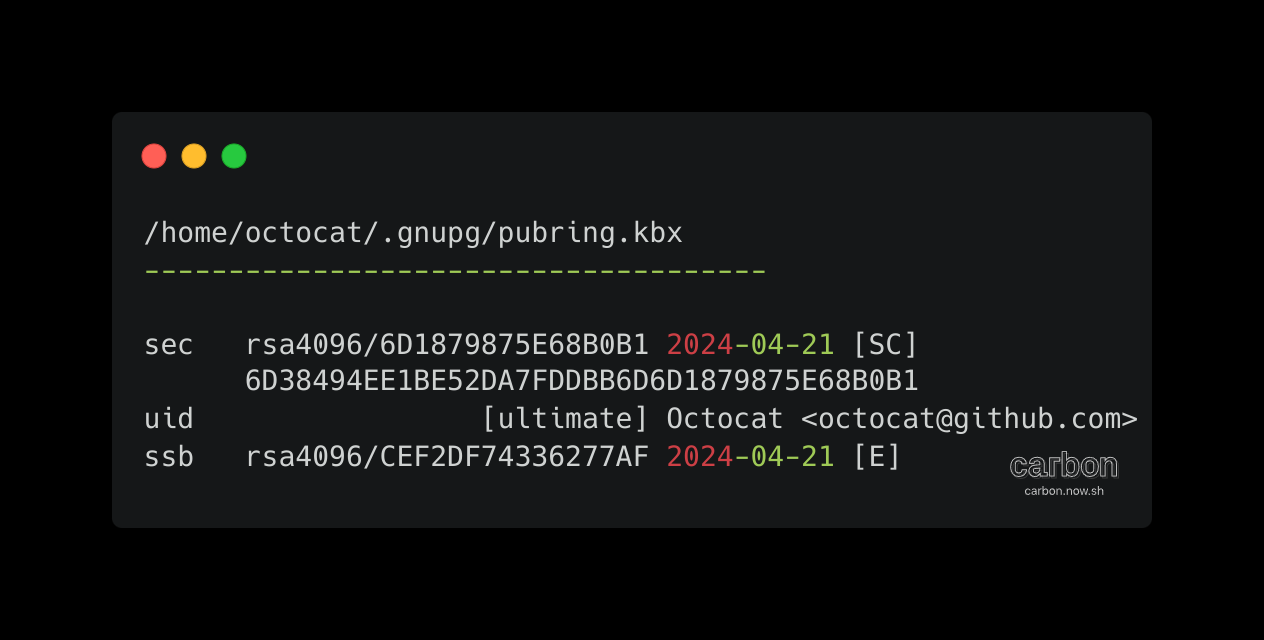
Use the gpg --list-secret-keys --keyid-format LONG command to list GPG keys for which you have both a public and private key. A private key is required for signing commits or tags. From the list of GPG keys, copy the GPG key ID you'd like to use. In this example, the GPG key ID is 6D1879875E68B0B1
gpg --list-secret-keys --keyid-format LONG
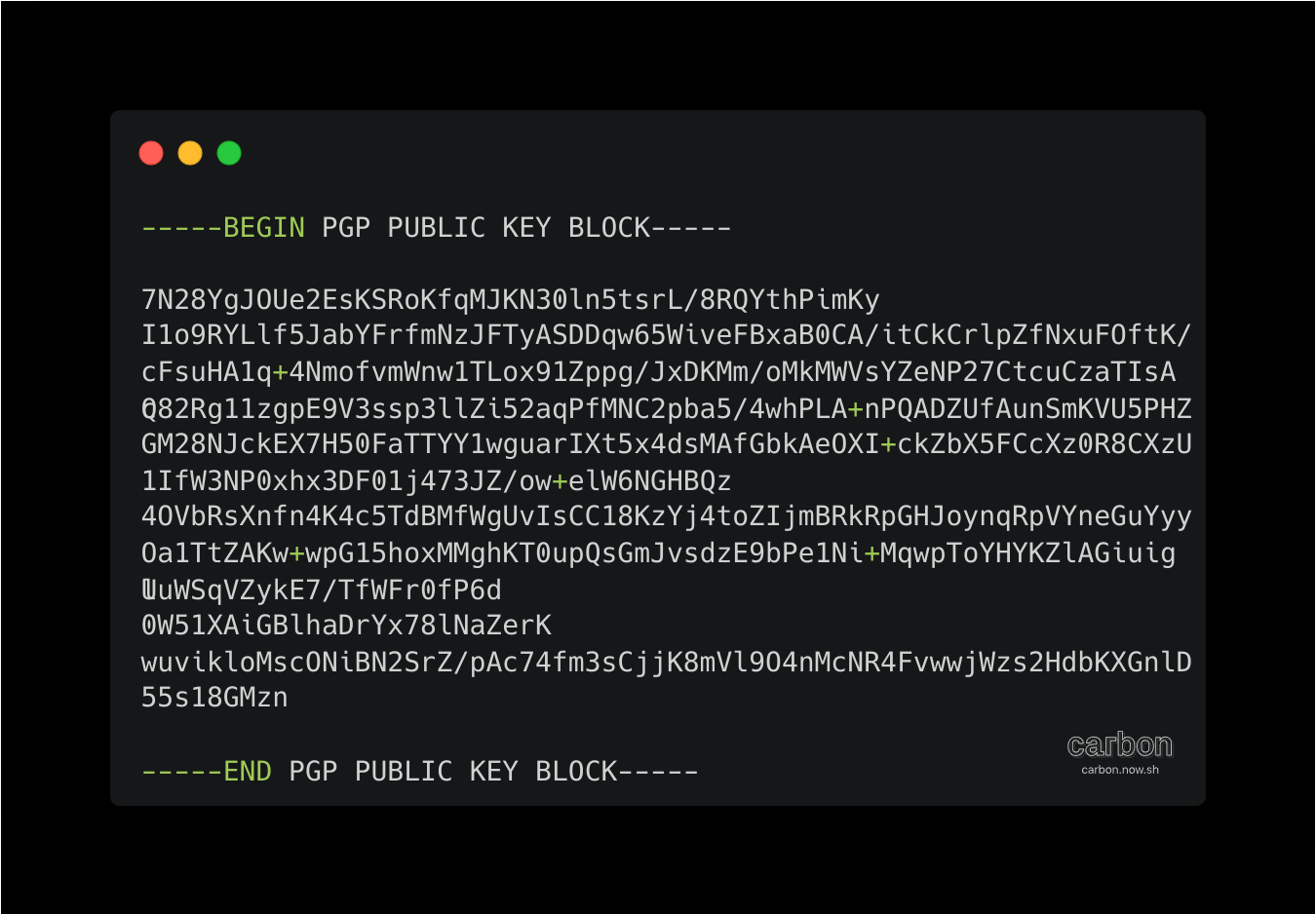
Paste the text below, substituting in the GPG key ID you'd like to use. In this example, the GPG key ID is 6D1879875E68B0B1
gpg --armor --export 6D1879875E68B0B1
Copy your GPG key, beginning with -----BEGIN PGP PUBLIC KEY BLOCK----- and ending with -----END PGP PUBLIC KEY BLOCK-----
Adding a new GPG key to your GitHub account
In the upper-right corner of any page, click your profile photo, then click Settings.
Click on SSH and GPG keys and add new GPG key.
In the "Key" field, paste the GPG key you copied when you generated your GPG key
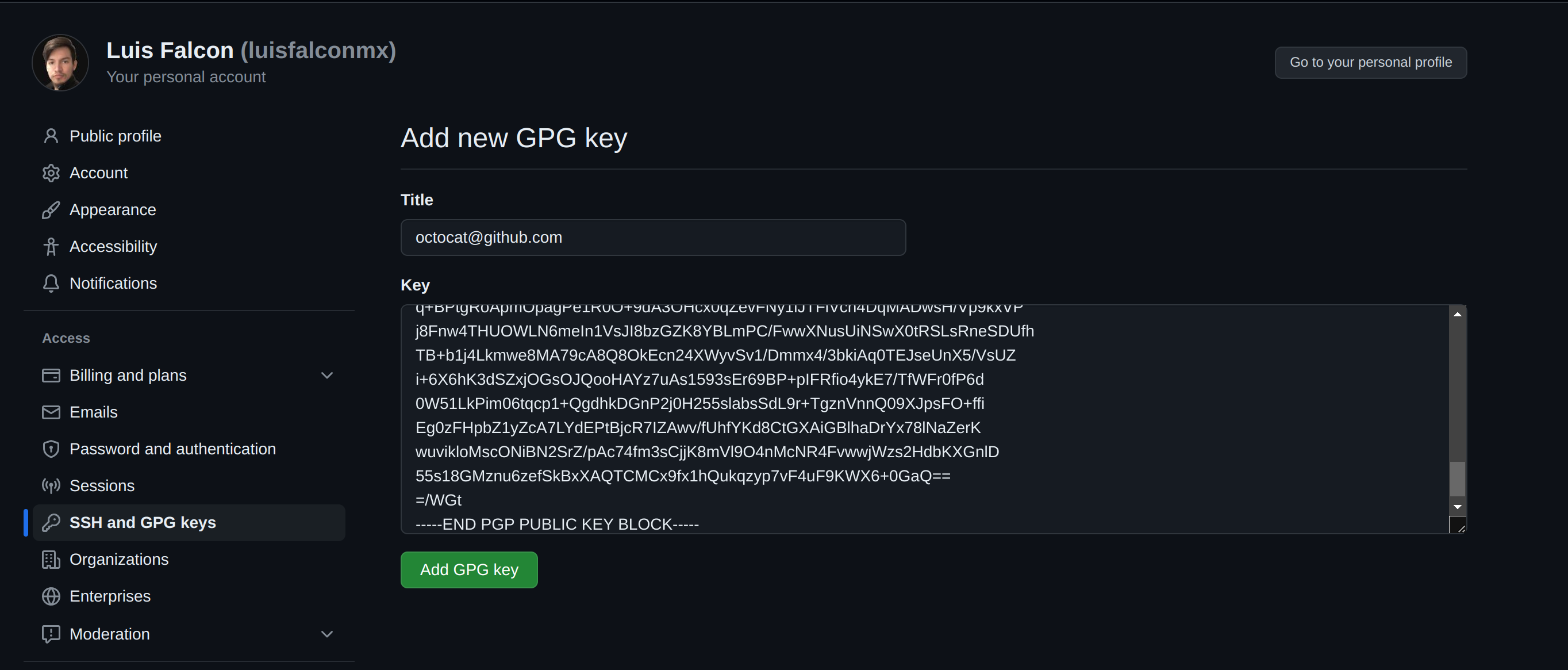
To finish, click on add GPG key and confirm the action with your GitHub password or your preferred auth method.
Getting GPG Keys
Open your terminal and use the gpg --list-secret-keys --keyid-format LONG command to list GPG keys for which you have both a public and private key. A private key is required for signing commits or tags. From the list of GPG keys, copy the GPG key ID you'd like to use. In this example, the GPG key ID is 6D1879875E68B0B1:
gpg --list-secret-keys --keyid-format LONG
Git Settings
To set your GPG signing key in Git, paste the text below, substituting in the GPG key ID you'd like to use. In this example, the GPG key ID is 6D1879875E68B0B1:
git config --global user.signingkey 6D1879875E68B0B1
To tell git to automatically sign commits you can set:
git config --global commit.gpgsign true
If you use Ubuntu you need to add the next line in your ~/.bashrc file.
# .bashrc
export GPG_TTY=$(tty)
Conclusion
Implementing verified commits using GPG is a proactive step towards enhancing the security and trustworthiness of your codebase. By adopting this practice, you not only protect your project from unauthorized changes but also contribute to a more transparent and accountable development process.
Throughout this guide, we've covered the essential steps for setting up and using GPG to sign commits effectively. Remember, verified commits not only benefit open-source projects but can also be valuable for teams working on proprietary software, ensuring that each commit is attributable and tamper-proof.
- GitHub
- Git
- Ubuntu
- Security
- frontend
- backend